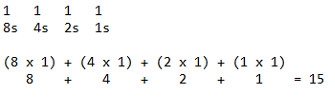Learn with mytechnotalent Free Course
This is my simple notes to learn using mytechnotalent free course for Reverse Engineering
You can learn more about this free course in his Github
Also don't forget to star his Github repo and subscribe his youtube channel which would be this
Thank you for your great course!
Lesson 1 : Goals
You can read more in here or in here
Malware analysis is the understanding and examination of information necessary to respond to a network intrusion.
Host-based signatures are also referred to as indicators which can identify files created or edited by the infected code which can make hidden changes to a computers registry.
Network signatures are used to find malicious code by examining network traffic.
Upon identification of these aforementioned signatures, the next step is to identify what the malware is actually doing.
UNDER NO CONDITIONS ARE YOU TO EVER USE THIS EDUCATION TO CAUSE HARM TO ANY SYSTEM OF ANY KIND AS I AM NOT RESPONSIBLE! THIS IS FOR LEARNING PURPOSES ONLY!
Lesson 2 : Techniques
You can read more in here or in here
Static analysis uses software tools to examine the executable without looking at the actual decompiled instructions in Assembly.
Dynamic analysis uses disassemblers and debuggers to analyze malware binaries.
Disassembler will convert an executable binary written in Assembly, C, C++, etc into Assembly Language instructions that you can debug and manipulate.
Lesson 3 : Types of Malwares
You can read more in here or in here
Backdoor is malicious code that embeds itself into a computer to allow a remote attacker access with very little or sometimes no authority to execute various commands on any respective local computer.
Botnet allows an attacker access to a system however receive instructions not from one remote attacker but from a command-and-control server to which can control an unlimited amount of computers at the same time.
Downloader is nothing more than malicious code that has only one purpose which is to install other malicious software and frequently installed when a hacker gains access to a system initially
Rootkit which hides the existence of itself and additional malware from the user which makes it extremely hard to locate.
can manipulate processes such as hiding their IP in an IP scan so that a user may never know that they have a direct socket to a botnet or other remote computer
Scareware is used to trick a user into purchasing additional software to falsely protect a user when there is no real threat whatsoever that exists.
Worm or Virus which copies itself and goes after other computers.
Lesson 4 : x86 Assembly Intro
You can read more in here or in here
x86 Assembly Language is a family of backward-compatible Assembly Languages which provide compatibility back to the Intel 8000 series of microprocessors.
used to produce object code for the aforementioned series of processors
uses mnemonics to represent the instructions that the CPU can execute.
Assembly Language for the x86 microprocessor works in conjunction with various operating systems
Linux runs on a variety of hardware and is capable of running devices such as a cell phone, personal computer or a complex commercial server.
The AT&T syntax was dominant in the Unix world since the OS was developed at AT&T Bell Labs.
Intel syntax was originally used for the documentation of the x86 platform and was dominant in the MS-DOS and Windows environments.
Lesson 5 : Binary Number System
You can read more in here or in here
Binary numbers are what define the core of a computer.
A bit within a computer is either on or off.
In decimal, base 10
number 15 which means (1 x 10) + (5 x 1) = 15 therefore the 5 is the number times 1 and the 1 is that number times 10.
Binary works in a similar fashion however we are now referring to base 2. That same number in binary is 1111.
Binary numbers are important because using them instead of the decimal system simplifies the design of computers and related technologies
To be continue..... (Last Update : 27 December 2020)
References
Last updated