HAC-SEC CTF 2021
A 24 hour Jeopardy CTF
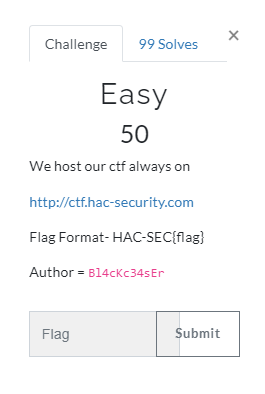
WEB
Easy
Open the link and we are redirect to the homepage again
Viewing the page source and find the flag format we can get the flag!
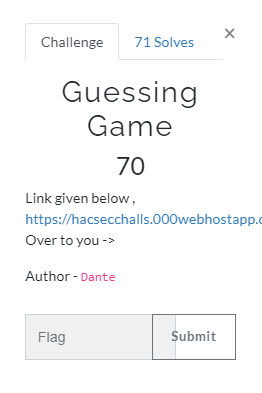
Guessing Game
The page seems down and I cant screenshot anything but to solve this challenge was to use guess parameter and try guess the numbers till you will get the flag!
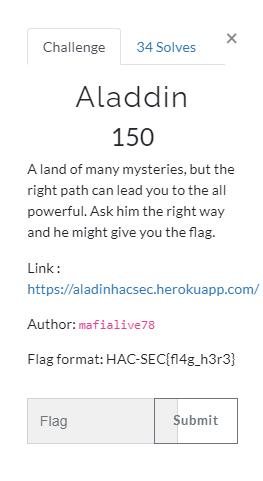
Aladdin
When we open the website it will redirect to use from 1.php to 17.php . So I create one liner command to get all the output.
And we will get output looks like this
Decode base64 we will get this
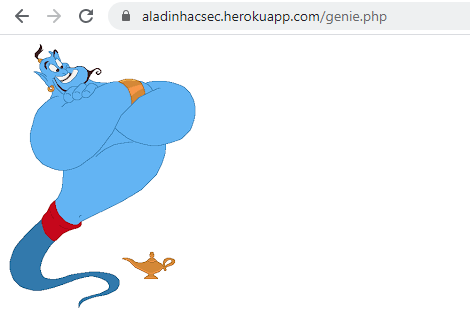
Going to /genie.php we found a site with genie
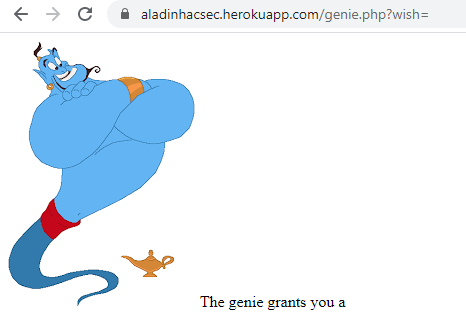
It seems like they might be parameter if we look back to what we decode from base64. Adding parameter wish will get genie to grants us something
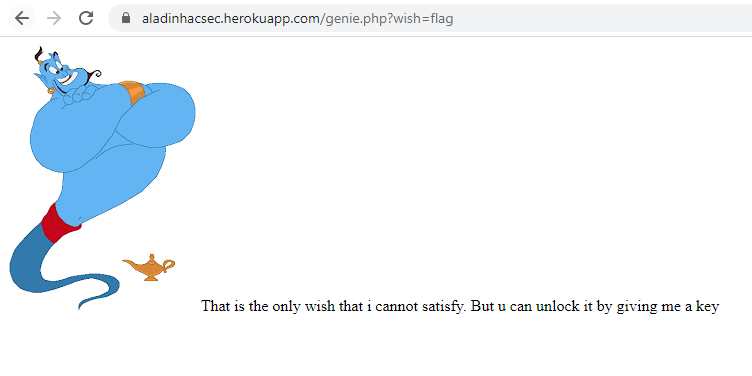
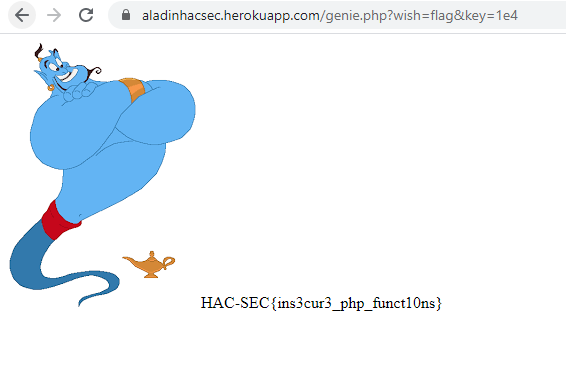
Let ask for flag >.<
Okay now he ask for parameter key? We tried with the parameter and here are the conditions
From this testing we found that by adding e which is equivalent to exponent we can get higher numbers. After a lot of tries 1e4 is the answer.
From what i think maybe behind it looks like this
Include
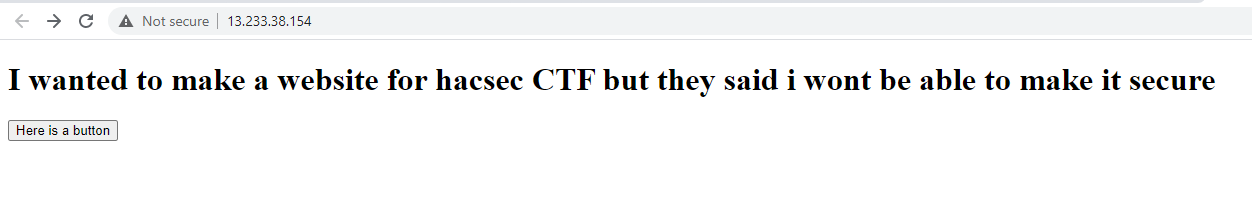
When we enter the site we will encounter this
By click the button it shows one parameter with an output.
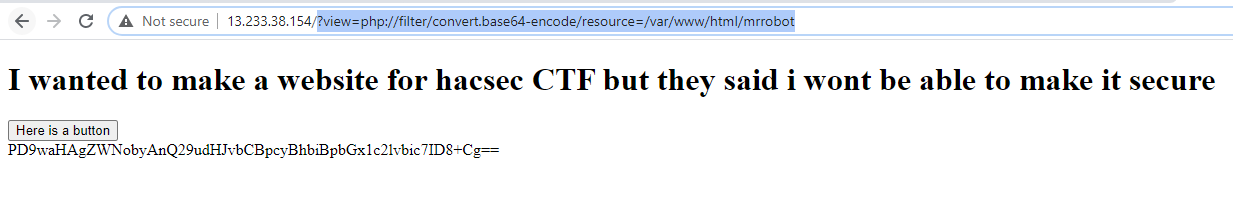
This looks like LFI ? Since mrrobot did not have any extensions we guess that it must add .php as default. Lets try use php filter and see the results
It works! It seems like it only echo the sentence. Now let's try to read index.php
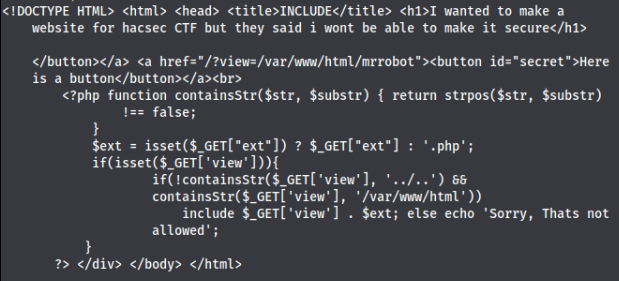
We will get this
From what we understand it should fulfill this requirements
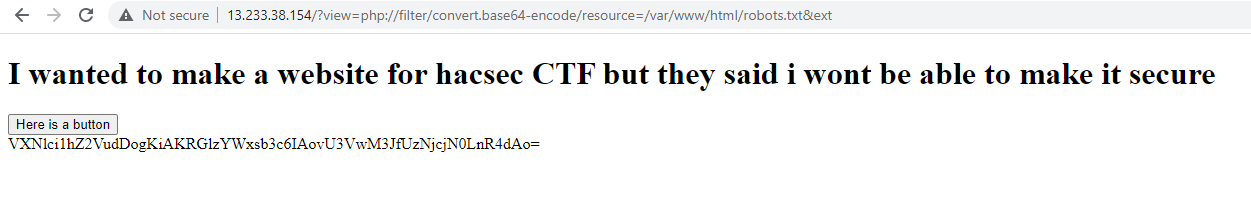
Based on this conditions we manage to bypass this and try to read robots.txt
We manage to get new file
Decode the base64 from that file we got
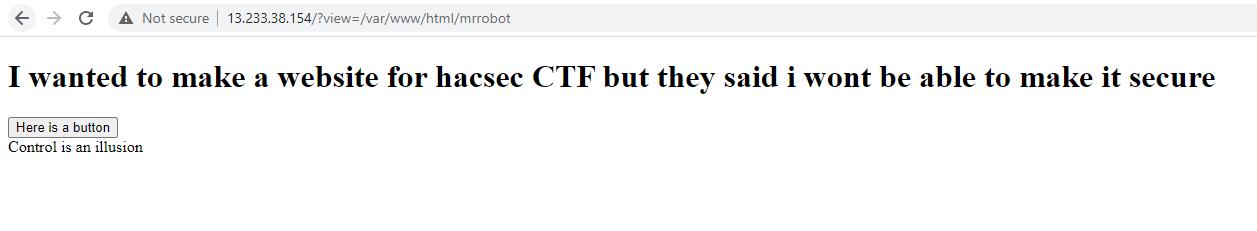
Since we can't use ../../ and we must include /var/ww/html in the parameter we found a solution for that
And we got the flag!
CRYPTOGRAPHY
It is a lottt!
We are given one file which content
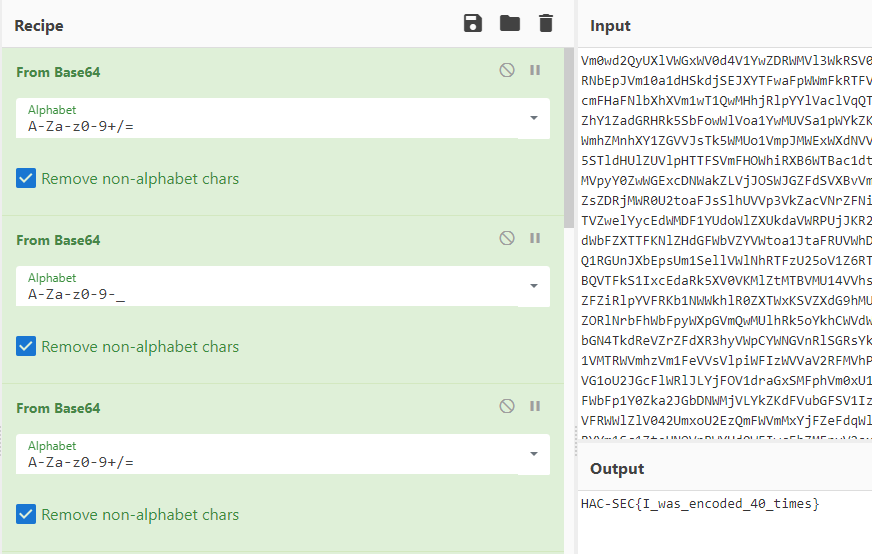
CyberChef identify this as Base64 , to get the flag we need to decode it numerous of times.
Jadoo Got Old
We are given one image file which content
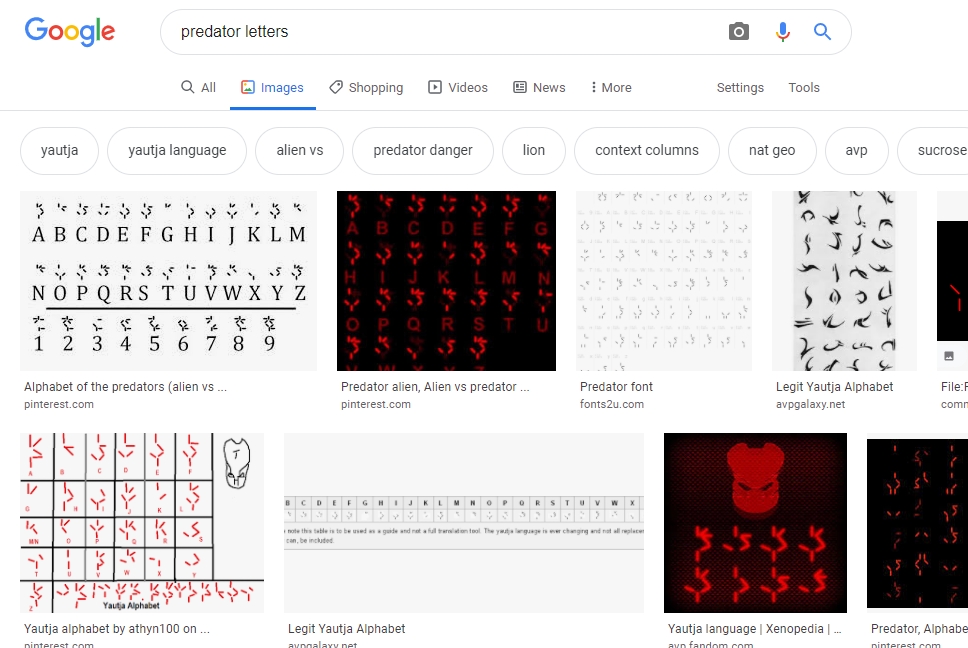
We have tried to search for a few keywords but predator letters give us one results
Looking at some images we found this
Let's try to decode it and we get the flag!
Last updated