PicoCTF 2021
Introduction
General Skills
Obedient Cat
Downloading the flag file we will get the flag!
Python Wrangling
We need to download 3 files
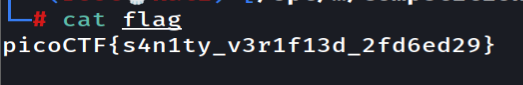
To solve it just run the python script like below
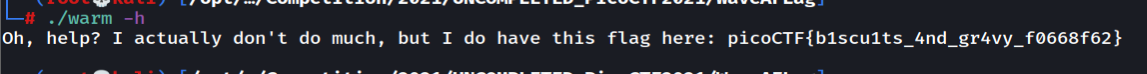
Wave A Flag
Download the file and since this is a binary do the steps beloww
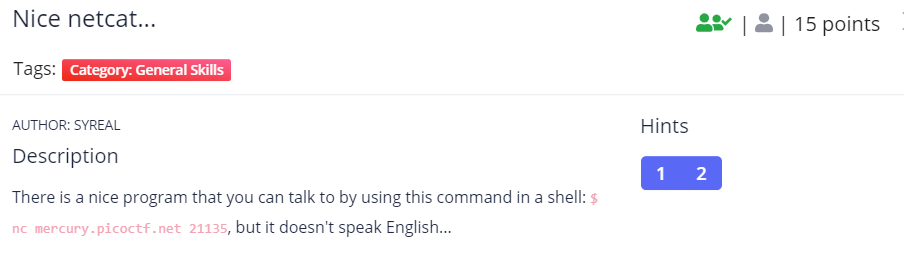
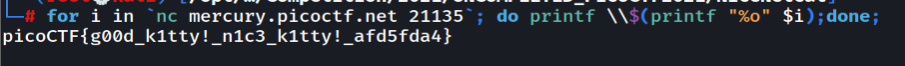
Nice Netcat ...
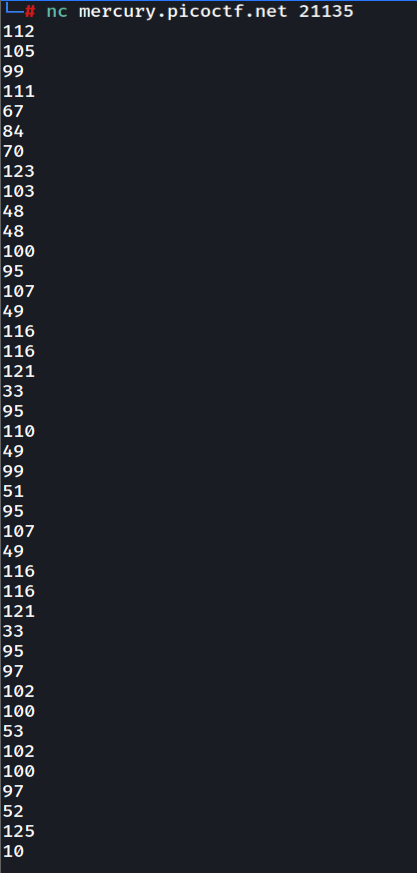
Netcat to the server will get us output like this
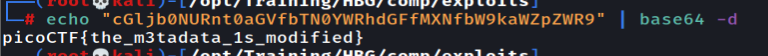
112 from decimal will get us p so we need to convert all of this to a flag format. Let's do it in a one-liner way :)
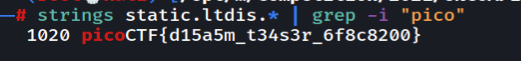
Static ain't always noise
Downloading the files you can just strings the files and get the flag but the intended way is to run the bash script with the static file as argument T
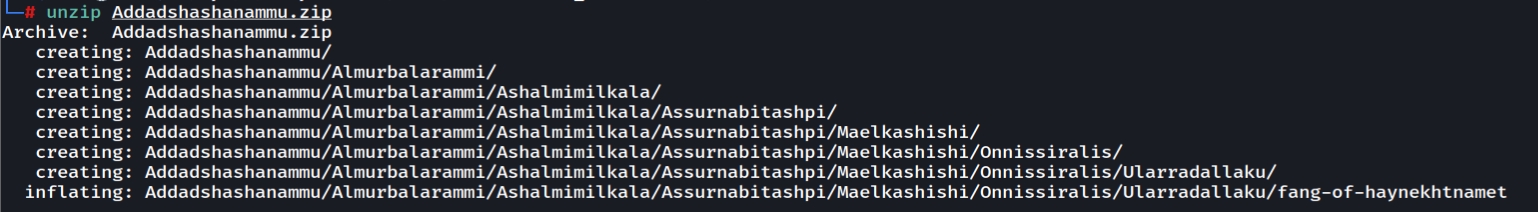
Tab, Tab, Attack
Downloading the files and unzip them will looks like this
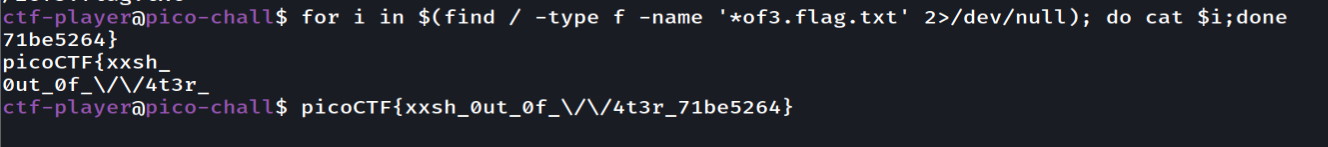
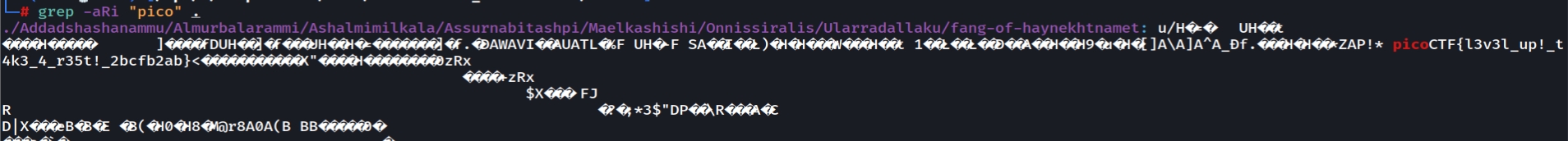
So let's recursively grep the flag format
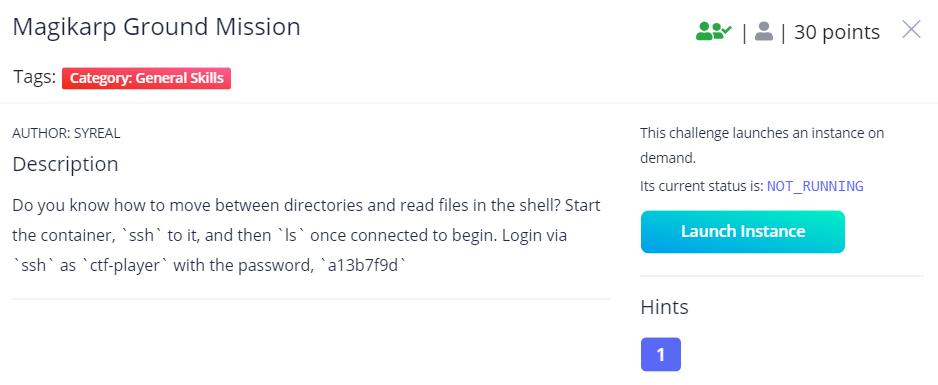
Magikarp Ground Session
Make sure to click Launch Instance first
Let's connect first to ssh
We need to find all of the 3 flags . This commands would help us
Web Exploitation
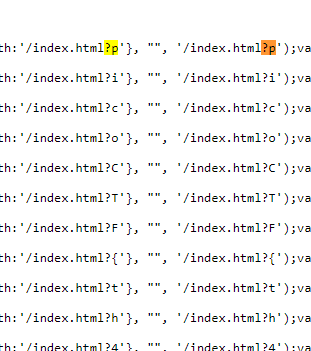
Ancient History
Looking at the page source. There is a lot of javascript. There is a lot of repeated javascript. But the url actually make us curious why its showing ?p so looking at the source code we found this
Let's use regex and grep this and combine as a flag
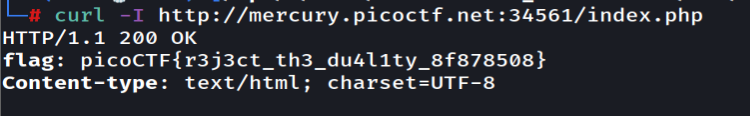
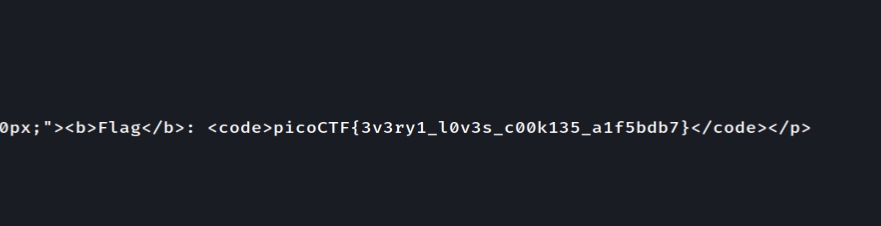
GET aHEAD
Going into the page we will see this
Since it saying head let's try show document info only
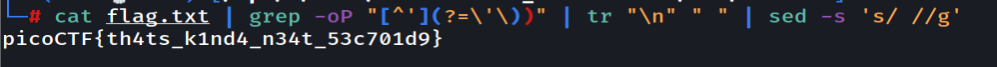
Cookies
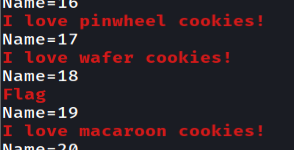
Playing with the web we found out that the cookie name can be manipulated to show different cookies. I love script >.<
Using name=18 will get us the flag
Scavenger Hunt
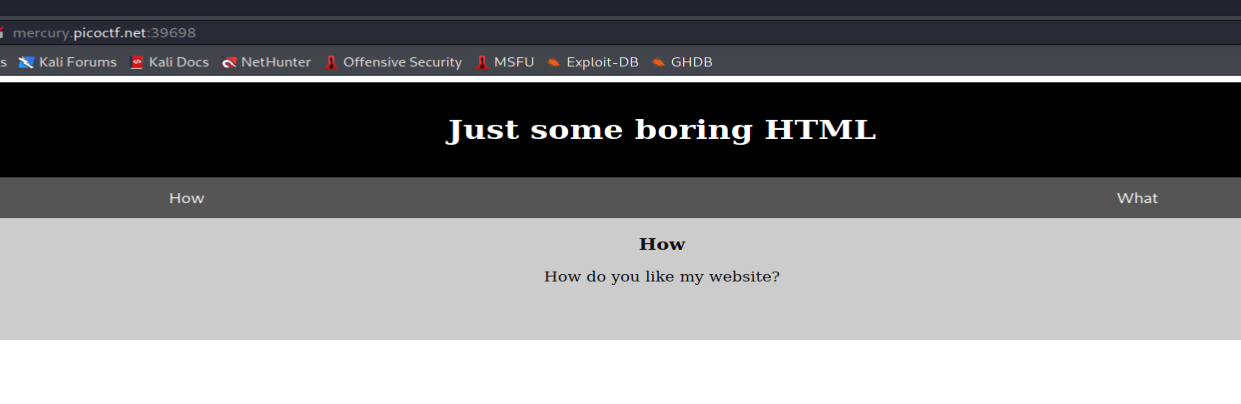
Opening the website we will see this
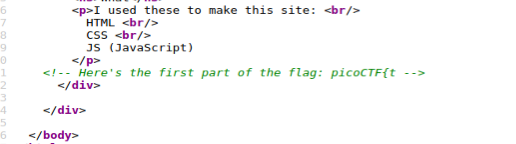
The first part we can get from the source code
The second part we can get in the css file
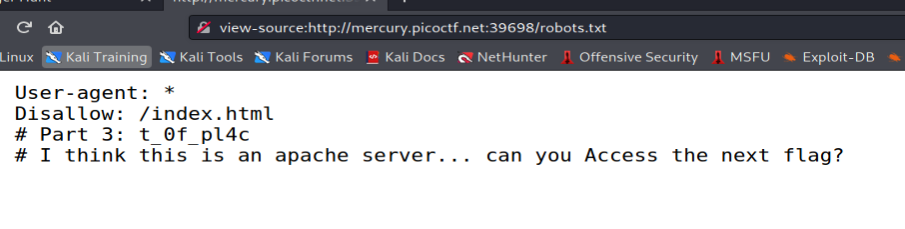
The third part we can get in /robots.txt
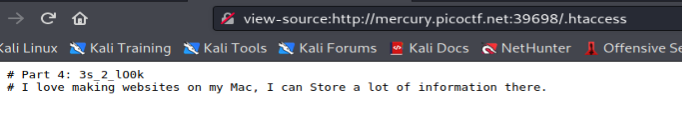
The fourth part we can get in .htaccess
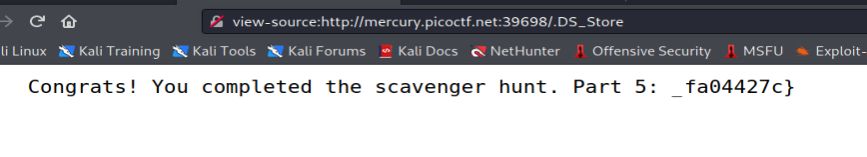
The last part we can take a look at .DS_Store
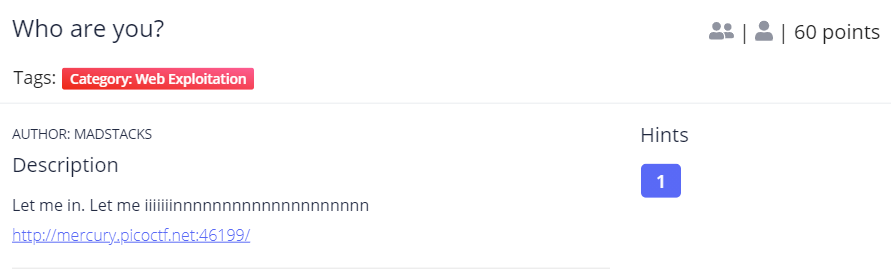
Who are you?
Looking at the web page we can see that it is required for us to use Pico Browser
As we manage to use PicoBrowser Agents we encounter another one which we need to access from trusted website only.
Also we manage to solve that but got another problem. Which this site is only worked in 2018.
Okay we got another problem. We need to ensure that we cant be tracked to access the page.
Reallly... We need to solve another problem which this site only for people from Sweden
Some Assembly Required 1
It is my Birthday
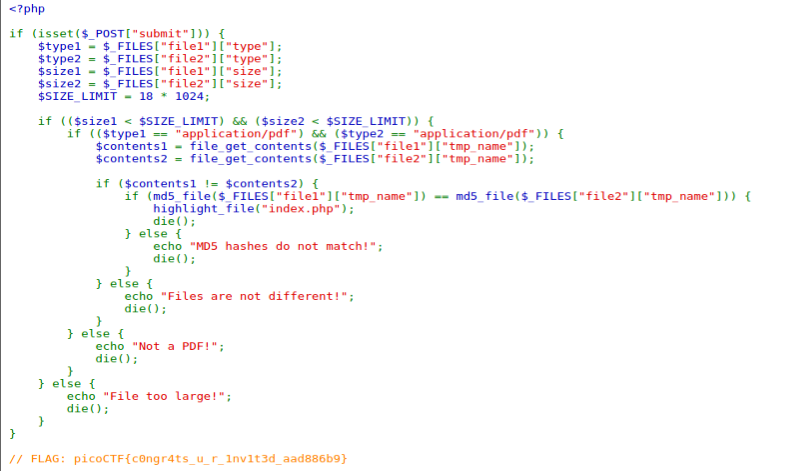
To solve it we just need to give 2 pdf file with the same MD5 hash value.
Some Assembly Required 2
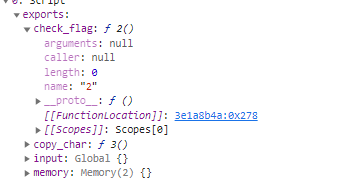
Open the web page and set breakpoints at line 34 and then check the web assembly
Which at the end we will see a possible flag?
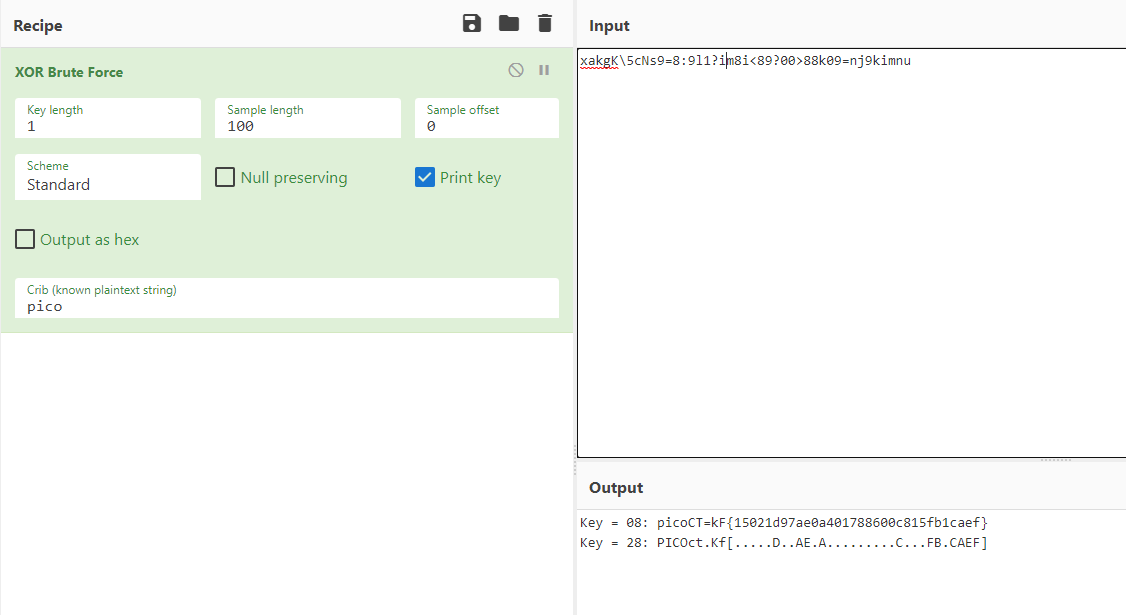
Trying bruteforce XOR will get us the flag
Super Serial
Going into the web page we can see a login page.
Most Cookies
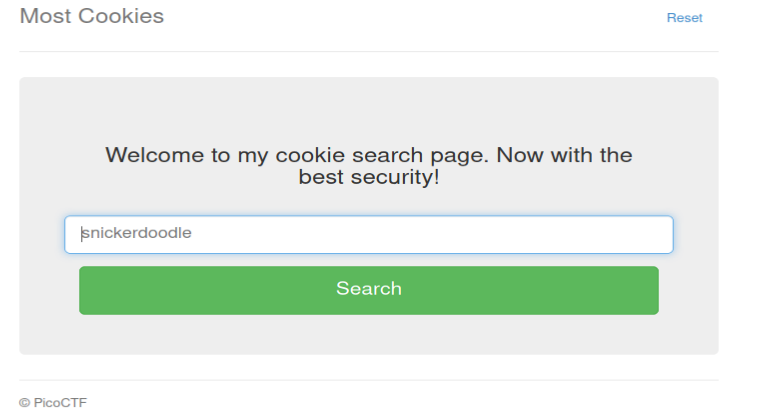
Looking at the page it almost same like before this
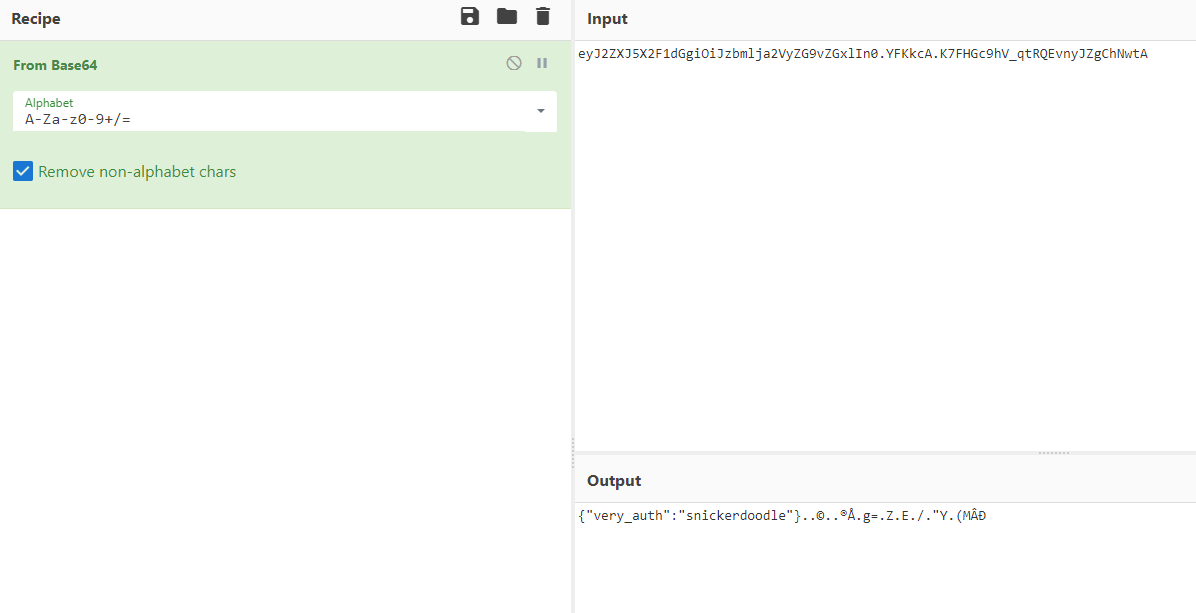
Trying to input snickerdoodle it give us a new session which after decode from base64 we will see this
The description of the challenge tell us about flask and the files that we download contains the secret key
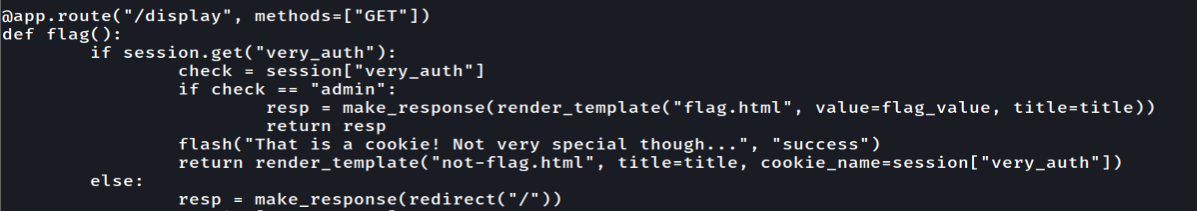
To get the flag we need to change the value of "very_auth" into admin
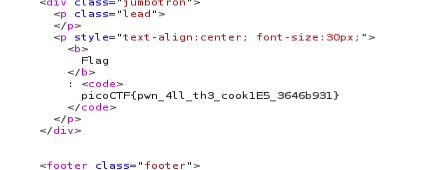
Change the session and we will get the flag!
Some Assembly Required 3
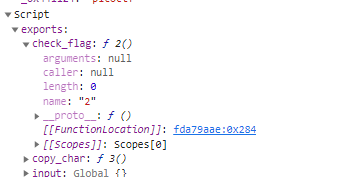
Set breakpoints at line 34 and we check this web assembly
But we can't do the same things in here. So let's save the file and save it as file.wasm and use wasm2c to convert it to c
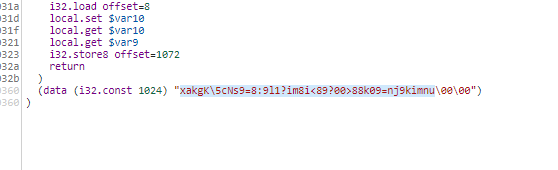
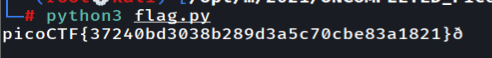
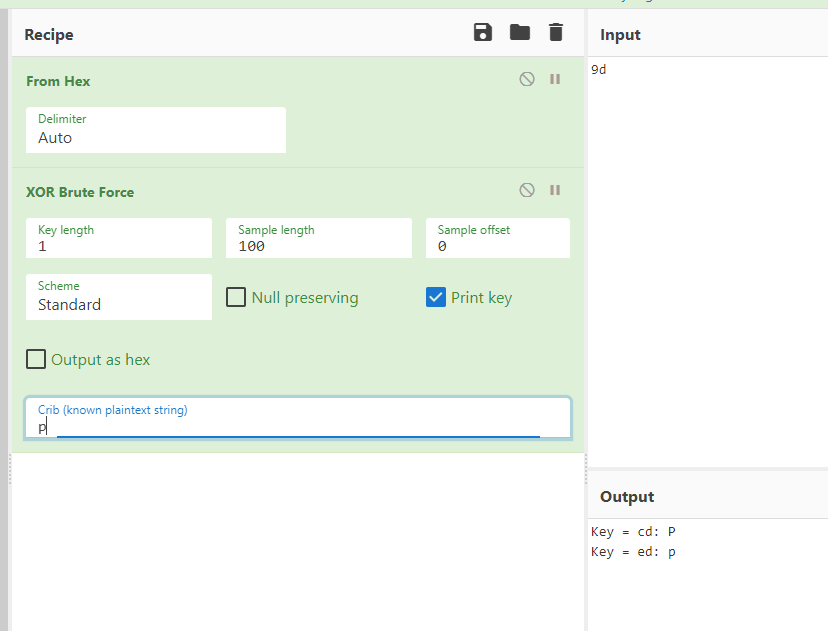
Since we know that the flag should be picoctf{ so what we did is check how the hex 0x9d can get into p
So actually it xor from left to right with the key that we have to here is a simple script to help us get the flag
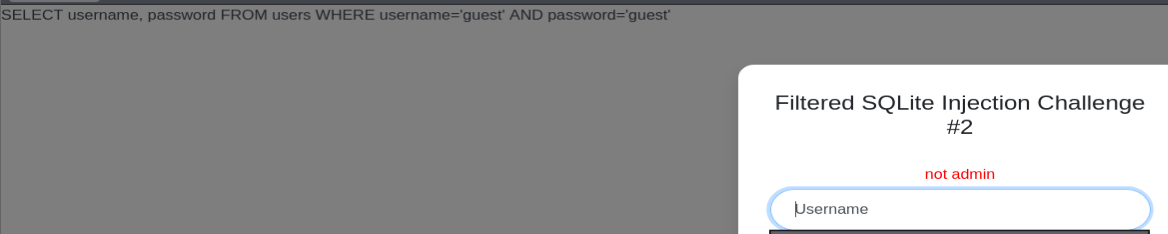
Web Gauntlet 2
When we open the page we will see a login page and input guest:guest give us a SQL Query behind
Startup Company
Some Assembly Required 4
Save the web asm we found and convert it using wasm2c
Cryptography
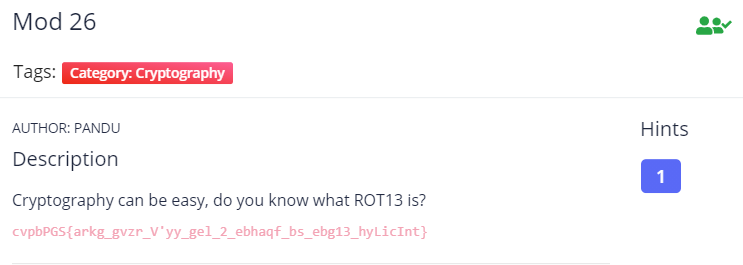
Mod 26
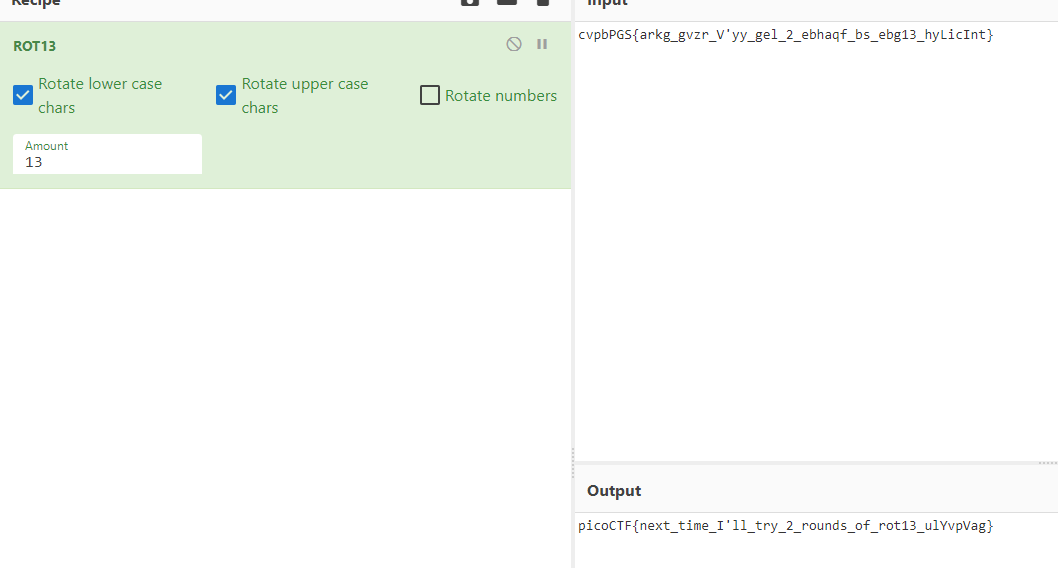
This challenge can easily solved using Cyberchef which is recipe of ROT13.
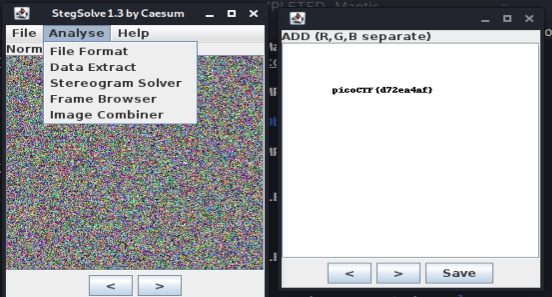
Pixelated
We are give 2 images in png format. This challenge can be solve by merge both images using StegSolve!
Forensics
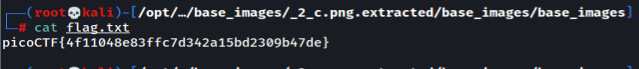
Information
Trying exiftool on the image we will find the flag
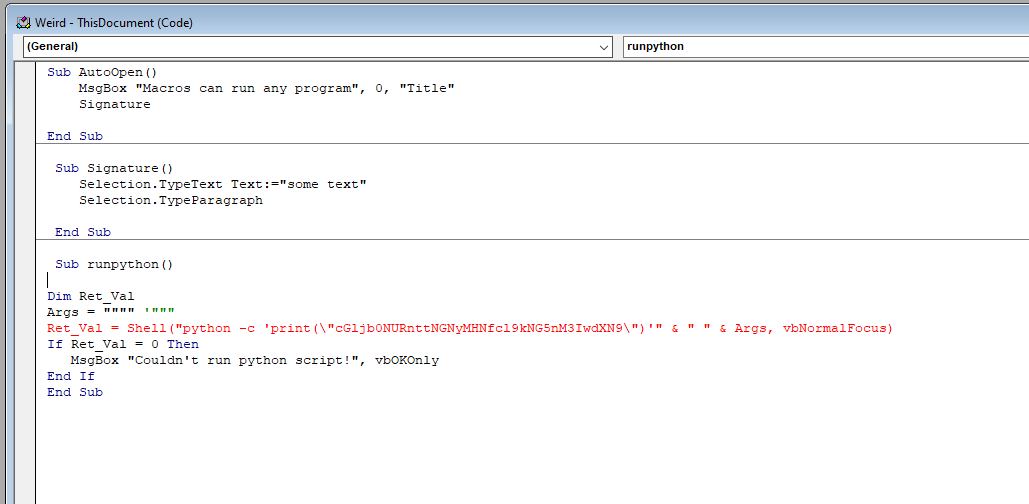
Weird File
Since this is a macro word file we can try open it and view the macros code
Matryoshka Doll
Unzip the files all the way and you will get the flag
Reverse Engineering
Last updated